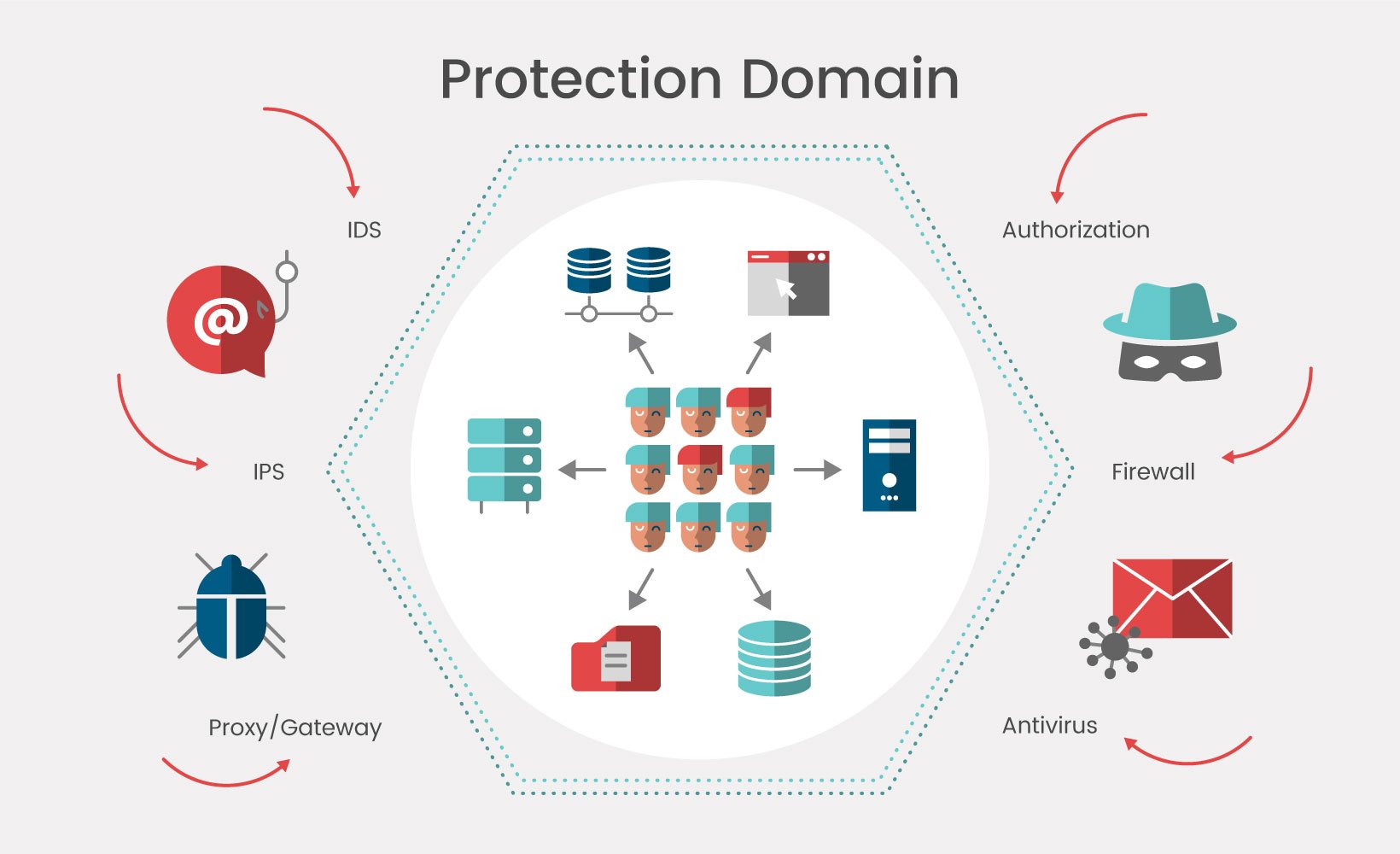
Position of e-StepControl solution in the overall security infrastructure
Contemporary information systems security tools allow avoiding external threats – hacking of passwords, e-mails with malicious attachments, DDoS attacks and other similar threats. At the same time, insufficient attention is paid to protection from internal threats, which are coming from internal authenticated users.
The problems of relevant control mechanisms lie in the fact, that authentication and authorization does not completely solve the problems of access control, because the restriction is usually applied to user's allowed activities, instead of objects themselves, which are used to perform the respective activities.
e-StepControl solution supplements the outline of the existing external security perimeter and allows to detect violations in activities of authenticated and authorized users. Moreover, this approach does not impose additional computing load on the protected system and does not interfere with daily activities of legitimate users in the protected IT system.